Whether you work in corporate government or private security it’s vital to stay one step ahead and identify hidden recording devices before they can compromise you. Detecting, locating, and identifying surreptitious surveillance devices has become more complex. Before the proliferation of active transmitters for information gathering purposes, the passive listening device was predominant. Such devices are not easily detected by conventional means due to their small size and low power consumption. A good understanding of radio frequency propagation is essential in planning surveillance activities either offensive or defensive. One must be able to determine the coverage area to ensure that transmissions are within range of the receiver site and that they are not being received by unintended parties. In addition one must be able to detect potential interception points when planning countermeasures or hire competent Technical Surveillance Countermeasures (TSCM) firm.
Such devices are not easily detected by conventional means due to their small size and low power consumption.
There are a number of ways to detect a bug, including:
- Visual detection: This method relies on the fact that bugs are often small enough to be visually detected by people and machines. A good example of this is an infrared camera, which can detect even the tiniest bugs with ease.
- Acoustic detection: An acoustic device uses sound waves from its microphone to determine whether there is a live recording device nearby (such as one hidden in your home). This machine works by detecting vibrations caused by movement within its surroundings—and if those vibrations are similar to those produced by audio signals then it will conclude that someone may have been eavesdropping on them!
A good understanding of radio frequency propagation is essential in planning surveillance activities, either offensive or defensive.
One must be able to determine the coverage area to ensure that transmissions are within the range of the receiver site and that they are not being received by unintended parties.
TSCM – Technical Surveillance Counter Measures (TSCM) Tools & Methodologies
- In the war on terror, there are many tools and methods used to combat terrorism. The most important of these is technical surveillance counter measures (TSCM). TSCM is a set of techniques that allow for the detection and neutralization of covert surveillance equipment. This can include both bugging devices and eavesdropping devices. TSCM should never be post-incident but an active standard operating procedure (SOP) applied regularly as part of their security housekeeping policy. The loss of sensitive company information can be down to a failure in internal policy, such as office refuge or key staff leaving.
- Spectrum Analyzer aka Radio Frequency Analysis: Spectrum Analyzer is a portable device with a rapid sweep speed and functionality suited for detecting unknown, illegal, disruptive, and anomalous rogue transmissions across a wide frequency range and detecting illicit eavesdropping signals, performing site surveys for communication systems, conducting radio frequency (RF) emissions analysis.
- NearField Detector : A NearField Detector is designed to detect low-level radio frequency (RF) radiation from transmitters, receivers, computers, etc. One of the two antennas detects towards positive while the other detects towards negative; as the ratio of the distance between the RF source and the antennas decreases, one antenna receives more RF than the other and the meter swings in that direction.
Non-Linear Junction Detector aka Electronic Device Detection A Non-Linear Junction Detector finds potential eavesdropping devices by flooding a suspect area or target with a spectrally pure microwave RF signal. It can detect Active or Live Bugs, Inactive Bugs, Turned On Bugs, Turned Off Bugs, Burned, Out Bugs or Dead Bugs.
Forensic Spyware Detection & Investigation: Forensic is normally not included in TSCM processes but encouraged to go deep into your technical devices operating in physical environment. Smartphones and computer equipment are functional and active within the office, home, and daily routines. Employees, Personnel, Officers. Third Party contractors should be involved in this process. Forensic investigation of such devices will reveal any suspicious activity considering surveillance or monitoring via malware or spywares to record or monitor surrounding.

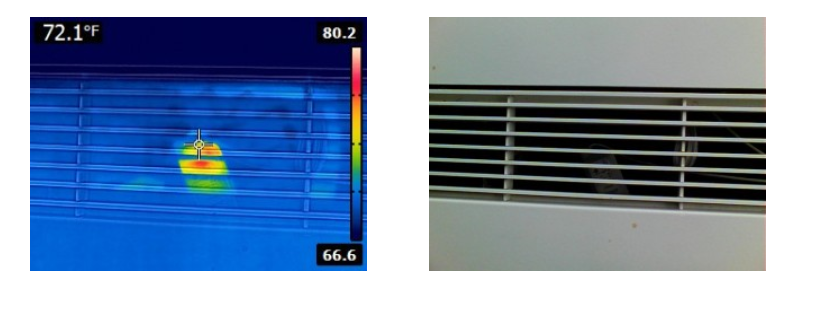
Signs Your Environment is Bugged
Secret meetings and bids seem to be less than secret.
Others know your confidential business or professional trade secrets.
You have noticed strange sounds or volume changes on your phone lines.
You have noticed static, popping, or scratching on your phone lines.
Read more at securitywall.co/blog

