WannaCry is now a hot topic in the cyber world as it is been reported in more than 150 countries around the globe, affecting thousands of machines and many companies with its encryption. The news came to circle when National Health Service (NHS) was under attack of WannaCry which it infected almost all National Health Service machines but steadily it spread into other parts of the country and then into other continents.
So a question arises how this all happened? The ransomware was first seen on Friday and spread rapidly through numerous substantial associations around the world. Not at all like earlier ransomware, this specimen utilized the SMBv1 "ETERNALBLUE" adventure to spread. "ETERNALBLUE" wound up noticeably open about a month back when it was featured by Shadowbroker part of NSA hacking tools.
Before going into detail, let's see how WannaCry work and how it can affect you.
How WannaCry Works & how it can Infect You
How to know if you are infected?
Systems that are infected by WannaCry will try to connect to a specific domain. Encrypted files will have the “wncry” extension.
Systems will scan internally for port 445
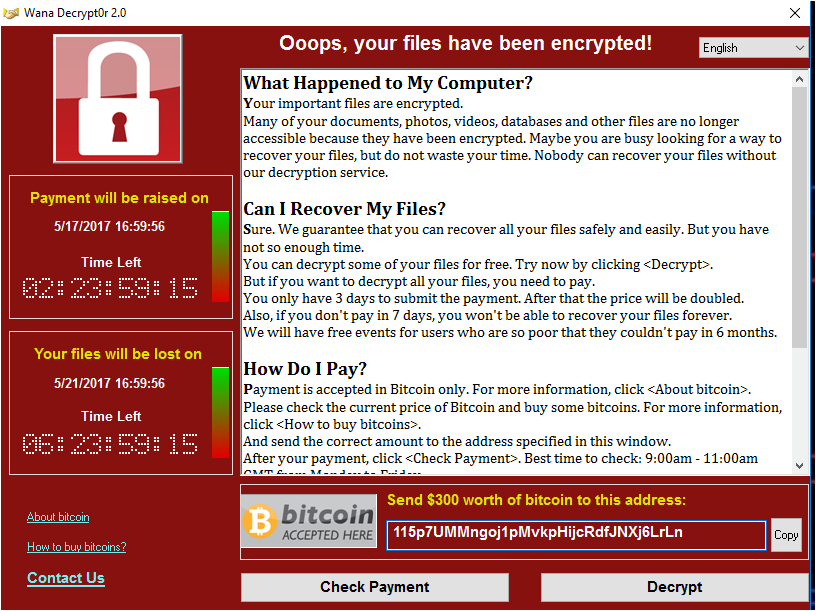
Ransom message will be displayed
In addition, infected systems will reach out to sites for crypto keys
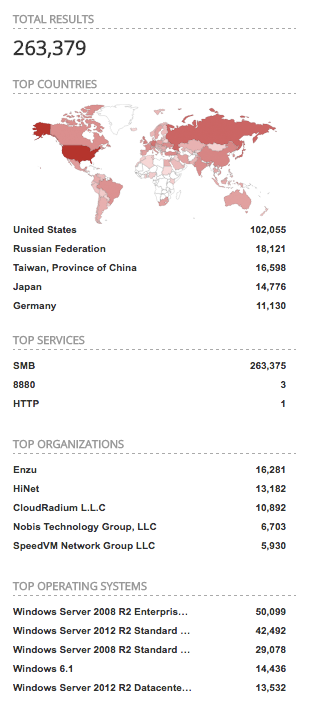
WannaCry Infection Stats
WannaCry HeatMap By Symantec
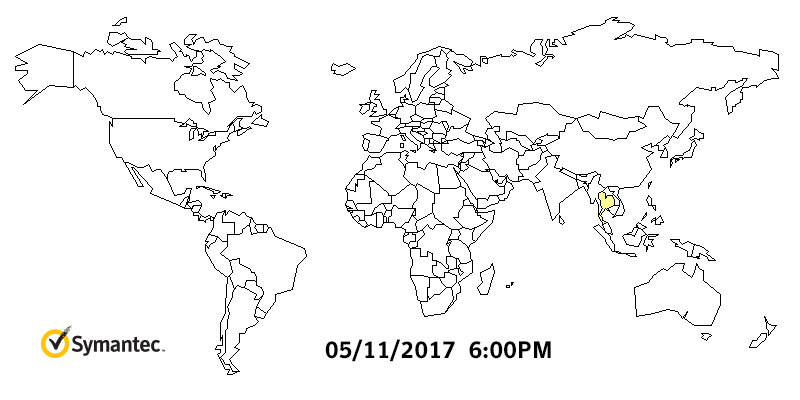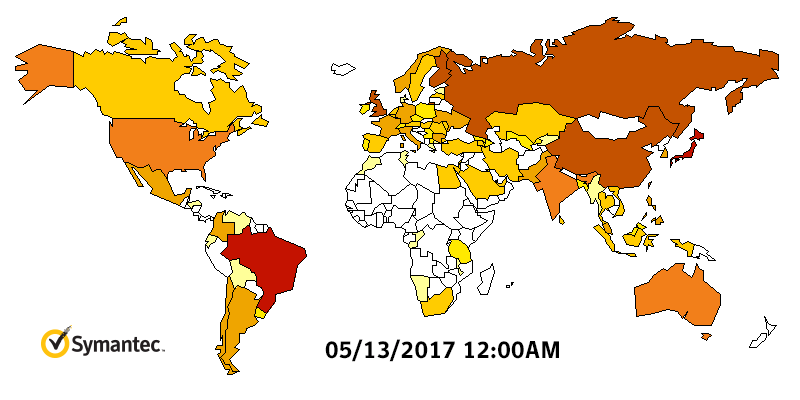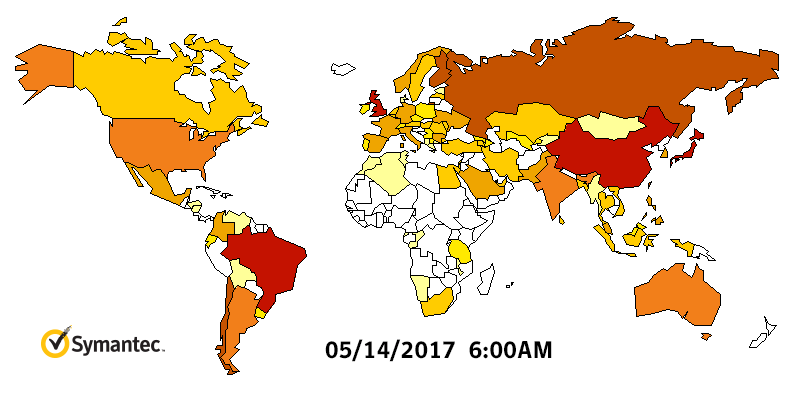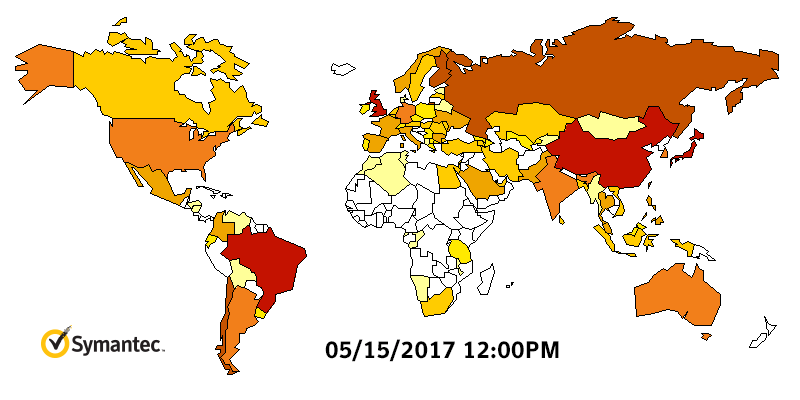
What if you are infected
Remediation
MS17-010 is known and infected which was fixed by Microsoft in March 2017. Also, Microsoft made fixes for its other OS, including Windows XP, Windows 8, and Windows Server 2003.
For the present, the best exhortation is to refresh your antivirus on endpoints, to guarantee that all Windows frameworks are completely fixed, to design firewalls to square access to SMB and RDP ports, and to teach clients to keep an eye out for suspicious messages.
It's striking that WannaCry introduces the DOUBLEPULSAR onto the infected machine. This is a piece mode payload that can subjectively infuse DLLs into the user.
Enable your machine Firewall and keep an eye on your ports traffic
Don't open any kind of Suspicious Emails or download suspicious file from any un-trusted Websites
Disable Server Message Block (SMBv1) protocol
This post is to aware normal users, system administrators, DataCenter, etc. We are coming up with full technical analysis in the coming days with more details.
Read about: Enhance Your Cybersecurity with SecurityWall: Pakistan Telecom Authority's Approved Cybersecurity Audit Firm