Since we all are stucked at home due to Coronavirus, So to maintain our work and communicate with team, workers, and employees we all are using video conferencing. Zoom got more popularity in these quarantine days for remote video conferencing and seems to be offering a lot. We can guess its popularity that even Boris Johnson uses Zoom for cabinet meetings. Things went crazy when their meeting id got public 539-544-323
A security issue in the Windows client of the popular video conferencing service that can be used for limited remote code execution and worse, to capture and replay security tokens to access network resources. It can steal windows passwords, can execute any program, etc remotely.
The app has a vulnerability in handling Uniform Resource Identifier paths, which can result in a Universal Naming Convention (UNC) injection.
The vulnerability was found by Matthew Hickey , G0dmode and reported to zoom.
How does it work?
Approach 1:
When sending a chat message, any URLs are converted into hyperlinks so that other people can click it and directly go to the webpage.
The problem is Zoom client for windows doesn’t validate the paths and lead Windows networking UNC paths into a clickable link in the chat messages as well.
Example: C:\Windows\Firmware can be sent to the chatbox as \\127.0.0.1\C$\Windows\Firmware
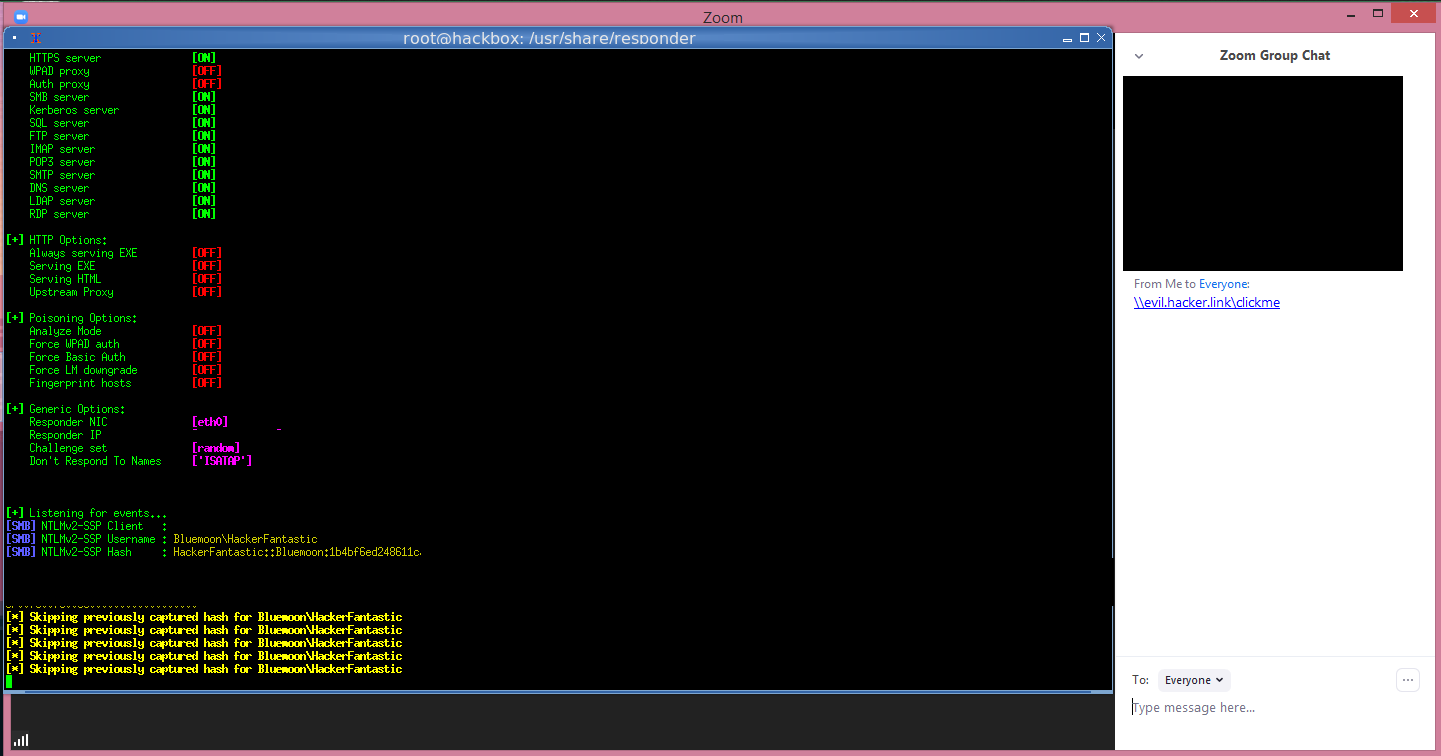
If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote file.
When doing this, by default Windows will send the user’s login name and their NTLM password hash, which can be cracked using free tools like Hashcat to dehash, or reveal, the user’s password.
Security Researchers tested the UNC injection in Zoom and were able to capture the NTLM password hashes being sent to a server hosting the clicked on share.
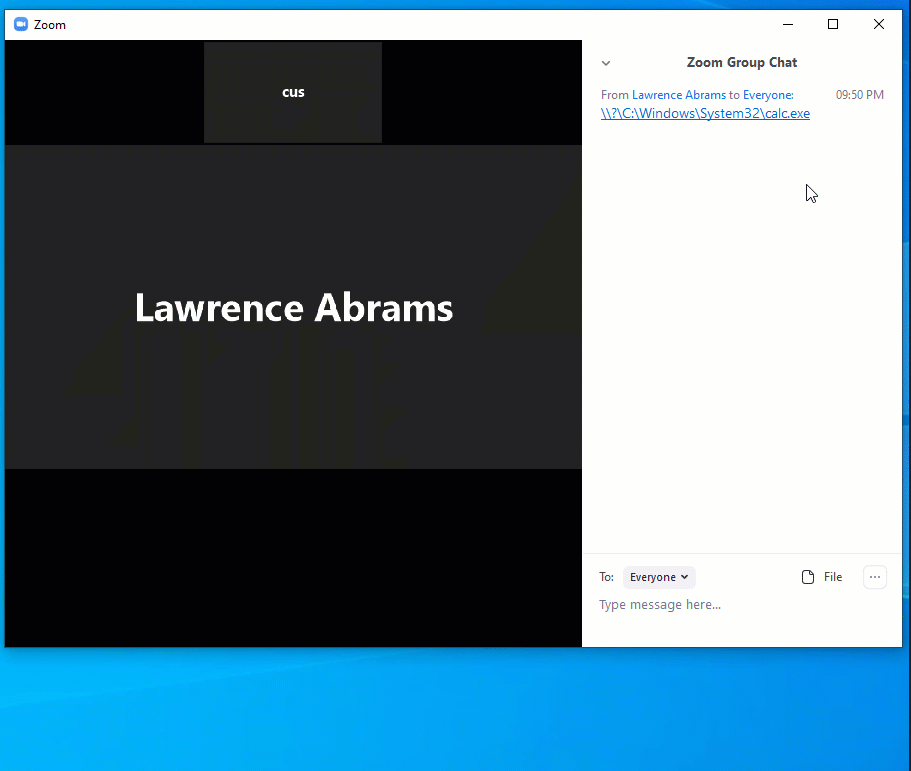
This is the Proof of Concept where I am -(attacker) opening calculator in victim PC.
On going story Jonathan Leitschuh a security researcher issued a proof of concept for the RCE vulnerability impacting 4+ Million of Zoom's users who have the Zoom Client installed on Mac. While Windows users are separate
The same vulnerability allowed to DOS any Zoom user.
<body>
<script>
// It's actually better if this number isn't a valid zoom number.
var attackNumber = "694138052"
setInterval(function(){
var image = document.createElement("img");
// Use a date to bust the browser's cache
var date = new Date();
image.src = "http://localhost:19421/launch?action=join&confno=" + attackNumber + "&" + date.getTime();
image.onload = function() {
// Be tidy, clean up the DOM afterwards
image.parentNode.removeChild(image);
};
document.body.appendChild(image);
}, 1);
</script>
</body>
Approach 2:
The best scenario which can work here can be:
\\?C:\Users\joe~1\Downloads\exploit.bat
Approach 3:
Through out there were a lot of new ways to exploit the bug which can trick user to click. Here we can see
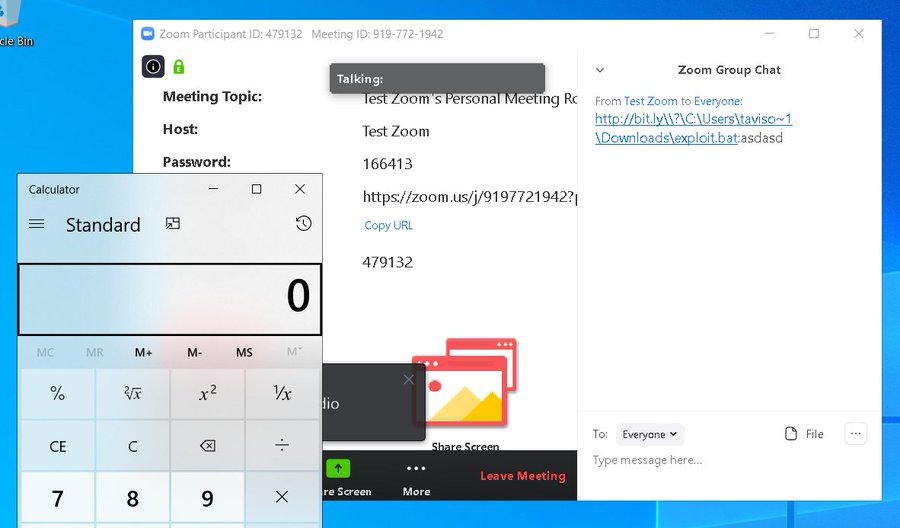
Approach 4:
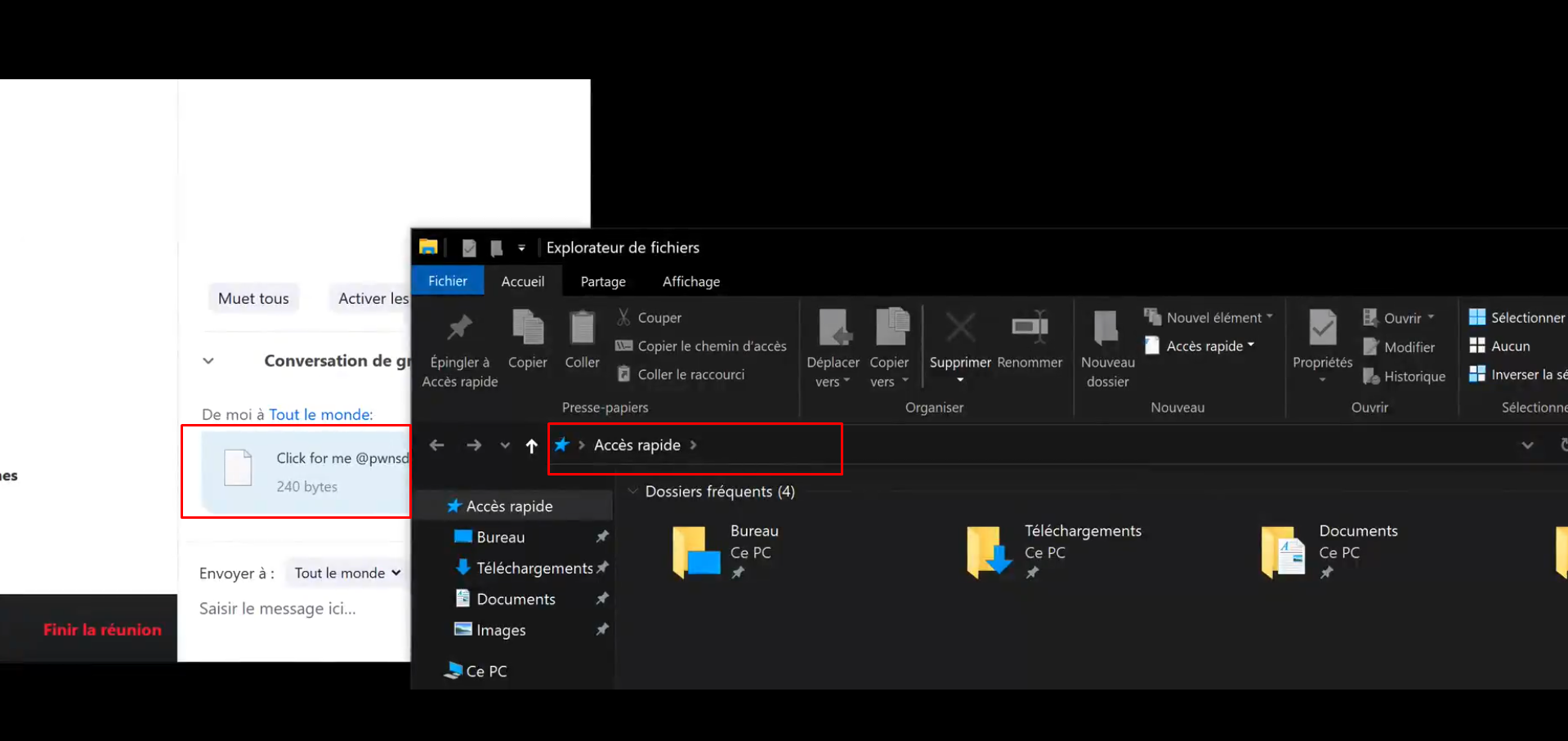
Zoom UNC Injection via Link Previews
But Why?
Upon reversing Zoom to investigate why it consider a URL as path, We made it to a conclusion.
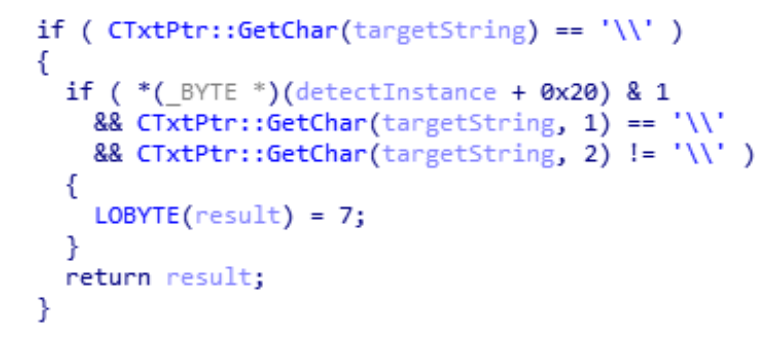
Zoom use Microsoft's RichEdit interface to process chat messages. Although Zoom allows only http: and https:, Microsoft hardcoded a check for UNC paths.Any chat message that starts with "\\" and has a third character that is not "\" will be considered a URL because of this reason. Through this we can access any global object via \\?\[object name], i.e \\?\C:\ Have a look
It didn't ended here, Uninvited guests who "zoom-bomb" online gatherings on Zoom have become a big enough problem that the FBI is on the case. Zoom had to update its software to prevent it from sending data from iOS device users to Facebook.
Zoom faces two additional security flaws that could be used to hijack a Zoom user’s Mac computer and access the webcam and microphone. Patrick Wardle, a former NSA hacker who works with Jamf, an Apple enterprise management software firm, revealed the bugs on his blog where it consist of multiple issues.
Local Zoom Security Flaw #1: Privilege Escalation to Root
Local Zoom Security Flaw #2: Code Injection for Mic & Camera Access
Both issues were so intense when it comes to an application which is used by million of people already and its usage it kept on increasing during on going pandemic to connect and do remote work through video conference. Vulnerability exploits a flaw in how Zoom handles the webcam and microphone on Mac's. Zoom, like any app that needs the webcam and microphone, first requires consent from the user. But Wardle said an attacker can inject malicious code into Zoom to trick it into giving the attacker the same access to the webcam and microphone that Zoom already has. Once Wardle tricked Zoom into loading his malicious code, the code will “automatically inherit” any or all of Zoom’s access rights, he said — and that includes Zoom’s access to the webcam and microphone.
If you care about your security and privacy, perhaps stop using Zoom - Researchers said.
Is there any mitigation?
They fixed in the new release, there is a Group Policy that can be enabled that prevents your NTML credentials from automatically being sent to a remote server when clicking on a UNC link.
The policy is called ‘Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers‘, needs to be set to “deny all” and can be found under the following path in the Group Policy Editor:
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Option
Good News: If you use 127.0.0.1 in the payload is used to prompts on victim screen asking for yes or no but that can be bypass by putting localhost instead of 127.0.0.1 in the payload, it won’t prompt anything from victim side. But got fixed in the recent release.
Bad News: So after the update,There are several other ways to make the injection works, well but link previews by encoding into base64 so you can still manage to get the RCE in the latest update too.
Other researchers explore more areas in the software where a sent file can open victim machine file through UNC path rendering bug.
Many meetings were disturbed as Zoom meeting links were disclosed and index in Google where attackers used them to disturb meetings but when it comes to high numbers of users attackers can join through these URL's and sit back and listen to your private talk as in high number of users attacker can play disguise. Hackers would just need to generate a list of 9, 10, or 11-digit meeting IDs, and check whether they were valid or not. If they got a hit, the spies could then eavesdrop on the conferences, and access all the video, audio and documents shared throughout the sessions, although this was only if no password were set. Beside all many Zoom meetings were disclosed on Github and these links dont require passwords to join these meetings.
We cannot blame Zoom for its great product and convenient, But Zoom’s misleading security claims give users a false sense of security and privacy. Whether it’s hosting a virtual happy hour or a yoga class, or using Zoom for therapy or government cabinet meetings, everyone deserves privacy.
Now more than ever Zoom has a responsibility to its users at this pandemic time where many rely on it. For now, Zoom at your own risk.
Still using Zoom, Take care of few things:
Avoid sharing the link to your meeting publicly.
Don’t use a Personal Meeting ID; use a one-time Meeting ID and a meeting password.
Disable “Join before host.”
Disable “Allow removed participants to rejoin.”
Enable Waiting Room, as it allows you to approve attendees before they join.
Set screen sharing to “host only” (to avoid someone broadcasting annoying or inappropriate content).
Disable file transfer (to prevent the transfer of malicious files).
Once everyone has arrived, lock your meeting.

